Hackers Target Medical Staff on Linkedin
If you’re a professional of any sort, you’re likely to have a Linkedin profile. The social network acts as a way to keep professional connections from seeing all your blase personal posts on Facebook, while still maintaining a personal connection to network & use as references in the future. Think of your Linkedin profile as a living resume, portfolio & list of references.
That’s why it came as a surprise to me that hackers love Linkedin – after all, Linkedin doesn’t have nearly the vast accumulation of data that we so willingly give to Facebook & Twitter, and more often than not we’re not connecting anything financial to it. However, after 2 months of receiving connection invitations from clearly fake profiles, I started to wonder why they might be targeting me.
It boils down to this: if you are attached, however tenuously, to the medical field, you’re likely a target to hackers. I, being part of a company with the word “physician” in the corporate name, am now a target too.
We’ve dealt with this for years on with our website. At one point, we were getting somewhere between 50 to 100 attempts to ‘break in’ to the back end of our website on a daily basis. We’ve since dealt with that problem, but it seems now that we’ll be facing unwelcome advances on social media instead.
Why Are Hackers Targeting Medical Professionals on Linkedin?
Why do hackers target medical staff on Linkedin? Simply put: because your data provides insights they can use. If they are able to connect with you and see details on your profile, they’ve got a valuable chunk of information that they can use for phishing schemes. From Trevor Christiansen at SungardAS:
Here’s a look at LinkedIn through a hacker’s eyes. Conducting a search for a specific organization on LinkedIn will turn up any number of professionals’ profiles, some of which will include the person’s business e-mail address. Once a hacker has seen a few e-mail addresses for the same company, he’s learned the company’s e-mail address structure (e.g. firstname.lastname@companyname.com ) and can build an e-mail list of employees to target. In fact, hackers can successfully guess 50 to 60 percent of all employee email addresses using this method.
Next, the hacker will formulate a phishing or social engineering plan. Using his knowledge of your firm’s IT platforms, his scheme could take the form of an e-mail that directs his unsuspecting victims to a webpage requiring them to enter their username and password credentials, for example.
The hacker will avoid including IT staffers on his distribution list, as that’s too likely to raise red flags. But customer service, accounting, marketing, and human resources personnel make much more attractive targets. The hacker will create urgency and emotion with his request. And, finally, he’ll send out his bait, hook his targets and voilá: he’s gained a foothold, the first step to getting the access he needs to breach the network and steal valuable credit-card, social-security or other data stores. A company’s worst nightmare has just begun.
If you’re within the medical field, you’ve already had it stamped into your head that medical record & patient privacy are of the utmost concern. What you should also be taught is that electronic health records are often the targets of hackers aiming to steal and sell valuable medical data. Healthcare information has a much greater black-market dollar value than many other pieces of personal information- even surpassing credit card data. Typically EHR information yields $50 per record. This amount can be considerably more than what a social security number or credit card number yields on the black market, and it drives hackers to obtain this information any way they can.
So, if we put our thinking caps on for a second, it makes a TON of sense that hackers would try to connect with medical staff on Linkedin. They can gain access to your phone number, email address, even the contact information of people you know and work with. From there, a savvy hacker can devise a plan to gain your password, or the passwords of your connections, and potentially gain access to that sweet payload of medical data.
How to Spot and Avoid Connecting to Hackers on Linkedin
Ever wonder what a hacker looks like? You might be surprised.
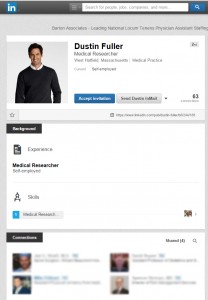
I’ve personally been getting connection requests from very attractive, self employed medical researchers lately. Normally, I accept most invites without even a second thought, unless they’re a life coach or clearly someone deep in the mires of MLM or pyramid marketing. However, the look of this ‘self employed medical researcher’ seemed familiar. I couldn’t place his face mentally, so I did a reverse image lookup to see if he was anywhere else on Google- he was, on the second page of a website selling business casual clothing to men. I didn’t accept that request and blocked the profile.
Over the next few weeks, more of the same kinds of profiles kept coming to me with invitations to connect. For the most part, I ignored them and didn’t think much of it. Then, today I got an invitation to connect from Dustin Fuller, another handsome self employed medical researcher… who happened to be connected to several physicians I know. I verified that “Dustin” was a model through a reverse image search, and then sent an email to my 4 shared connections connected to him:
“Do you actually know this Dustin Fuller, the self employed medical researcher that you’re connected to on Linkedin? Something weird is going on where I get requests from self employed medical researchers, all using a fake profile pic of some male model. I’ve been deleting the requests after someone in a forum said something about them being hackers or something, but I keep seeing my connections linked to them on Linkedin so I’m double checking. this is the profile of the Dustin Fuller character: https://www.linkedin.com/pub/dustin-fuller/b8/244/188”
Almost immediately, I got a response from one of my connections:
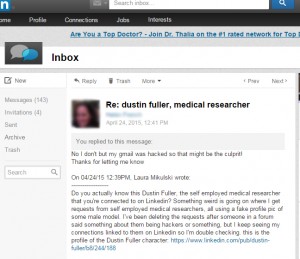
Thanks for letting me know”
So, now I know I’m not losing my mind at least, and hopefully a few people have been warned.
I’m still a firm believer in connecting with most people who request the connection- after all, you never know what they might add to your life. However, these incidents are pretty telling, and sent up major red flags with me. Here’re the big red flags that made me decide not to connect to this person:
- Fake profile picture: seriously, no self employed medical researcher looks like that. The picture wasn’t such a huge impediment, but when it was coupled with the items below it rounded out the notion that this profile was nothing but trouble. I wouldn’t have even done a reverse lookup if the rest of the red flags weren’t there.
- Few or no connections: the first attempt the hacker made was from a profile with no connections. Unless I personally know someone, I’m never going to connect to someone who has zero connections.
- No contact information: no email or phone number or way for me to verify this is a real person.
- Slim details: again, someone who is trying to establish new connections in general is going to have more than just their title and the fact that they’re self employed listed on their Linkedin.
It should go without saying that everyone should be careful with who they share information with online; however, medical professionals NEED to know they’re actively being targeted. When in doubt about a new connection on Linkedin, send them a message asking who they are and for any identifying info before you connect. If they don’t respond, or their response is insufficient, don’t connect and actively report them as spam on Linkedin. Remember- what seems like every day data to you can be a goldmine for someone with a malicious agenda.


Comments
No comment yet.